Blog
Data Breach
Section titled “Data Breach”🔐 Trends, Costs & Mitigation Strategies
It’s no longer a question of if, but when data breaches will occur. And their financial consequences are escalating rapidly.
📊 Key Statistics
- 68% of breaches involve human error (phishing, stolen credentials).
- Software vulnerability attacks up 180%.
- AI-driven phishing campaigns surged 4,151%.
💸 Average Breach Cost by Sector
| Sector | Average Cost |
|---|---|
| Healthcare | $9.77M |
| Finance | $6.08M |
| Energy | $5.94M |
| Manufacturing | $5.56M |
| Government | $2.55M |
⏱️ Containment Time
- Average time to contain a breach: 258 days.
- If contained within 200 days, organizations save $1.39M.
🛡️ Top Mitigation Strategies
- Automation & AI → 31% cost reduction.
- Zero Trust Architecture → essential for finance & public sector.
- Network segmentation + MFA → critical for healthcare & retail.
- Continuous employee training → your first line of defense.
📅 Published on: August 2025
📣 Hashtags: #Cybersecurity #DataBreach2025 #RiskManagement #AI #ZeroTrust #Infosec

Age Verification Online
Section titled “Age Verification Online”🔐 Protecting Minors or Risking Digital Freedoms?
More and more countries are introducing laws to verify users’ age online, aiming to shield minors from harmful content such as pornography, gambling, violence, and eating disorders. But the debate is far from settled: are we truly building a safer internet, or paving the way for new forms of surveillance and discrimination?
🌍 Country Approaches to Age Verification
| Country | Measure |
|---|---|
| 🇫🇷 France | Access to adult sites blocked without age verification. |
| 🇪🇸 Spain | Upcoming law mandates parental controls for social media. |
| 🇮🇹 Italy | AGCOM introduced an anonymous verification system to protect user privacy. |
| 🇬🇷 Greece | Launched the KidsWallet app to help parents monitor online activity. |
| 🇩🇰 Denmark | Proposed ban on social media for users under 15. |
| 🇬🇧 UK | Online Safety Act requires ID checks via documents, selfies, or digital IDs. Users already bypassing it with VPNs and tricks. |
| 🇦🇺 Australia | Law bans social media access for under 16s, with fines up to $49.5 million for non-compliant platforms. |
⚠️ Key Concerns
- Privacy: who controls the data collected for age checks? For how long? Under what safeguards?
- Algorithmic discrimination: facial recognition or digital ID systems may exclude users without proper documentation or devices.
- Digital exclusion: vulnerable youth risk being further marginalized.
- Future use of data: sensitive age-related data could be repurposed for profiling, targeted ads, or even discrimination in services, employment, or credit.
🎯 Protecting minors is essential.
But we must carefully consider how to do so without compromising fundamental rights like privacy, inclusion, and freedom of expression.
📅 Published on: July 2025
📣 Hashtags: #DigitalSafety #Privacy #OnlineAgeVerification #MinorsOnline #OnlineSafetyAct
Privacy-Focused Search Engines
Section titled “Privacy-Focused Search Engines”🛡️ In an era of increasing digital surveillance, choosing a search engine that respects your privacy is a strategic move.
✅ Alternatives to Google and Bing
| DuckDuckGo | Does not track or store personal information. Blocks website tracking. |
| Brave Search | Uses its own index. No tracking or profiling. Offers unbiased, uncensored results. |
| Mojeek | Independent crawler and index. Delivers unbiased search results. |
| Qwant | European engine with strict GDPR compliance. Privacy-first by design. |
| Startpage | Acts as a proxy for Google results. Anonymizes queries and IP addresses. |
| Swisscows | Based in Switzerland. Family-friendly and privacy-focused. |
| Kagi | Paid service with anonymous searches. No data storage. Uses its own index and anonymized APIs. |
🔐 Key Features to Look For
- No IP address logging: Your IP should never be stored.
- No search history tracking: Searches must not be linked to your identity.
- No personalized ads: Ads should reflect current queries, not past behavior.
📅 Published on: June 2025
📣 Hashtags: #Privacy #SearchEngine #DataPrivacy #OnlineSecurity #PrivacyMatters #GDPR
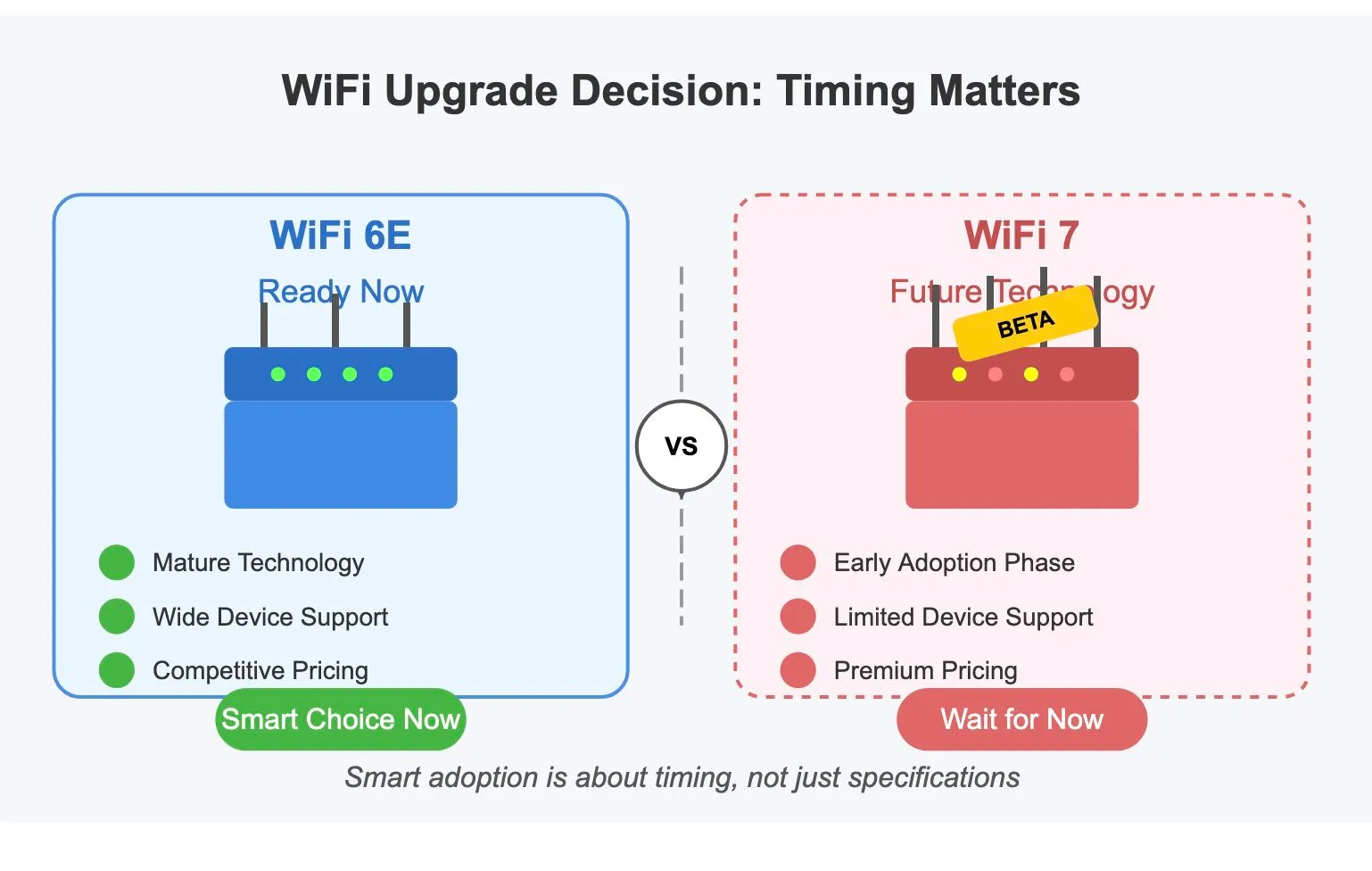
WiFi 7 vs WiFi 6E
Section titled “WiFi 7 vs WiFi 6E”📡 Why Jumping to WiFi 7 Might Not Be the Smart Move Just Yet
📶 While the tech world buzzes about WiFi 7’s impressive capabilities, patience may be the wiser approach for most businesses and individuals.
✅ Strategic Perspective
| Topic | Insight |
|---|---|
| WiFi 6E maturity | Tri-band WiFi 6E offers stable drivers, broad device support, and proven reliability |
| Ecosystem readiness | Competitive pricing and mature deployments make WiFi 6E a safe investment |
| WiFi 7 limitations | Still in early adoption phase; standard not finalized; firmware and device support immature |
| Performance reality | Gains are mostly theoretical for typical business/home use cases |
| Adoption strategy | Smart tech decisions prioritize reliability and cost-efficiency over hype |
| Future outlook | WiFi 7 is transitional—WiFi 8 may be the real leap (expected ~2028?) |
💬 Conclusion
Smart technology adoption isn’t about chasing specs—it’s about deploying solutions that work. For now, WiFi 6E delivers. WiFi 7? A future-focused investment still waiting for its moment.
📅 Published on: May 2025
📣 Hashtags: #Networking #WiFi #TechnologyStrategy #DigitalInfrastructure #TechTrends
AI Image Generation: Beauty and Risk
Section titled “AI Image Generation: Beauty and Risk”🎨 The generation of images through AI—like the recent Studio Ghibli style trend—is fascinating.
🚨 But be mindful of the risks that come with this creative power.
| 📢 | Non-transparent storage | Uploaded images may be stored and reused for unknown purposes |
| ⚠️ | Deepfake expansion | Generated or uploaded images could be manipulated to create fake content |
| 🗂️ | Sensitive data exposure | Hidden metadata (location, date, device) may reveal personal information |
💬 Conclusion Don’t worry! If your photos are already in the cloud, the line between ‘private’ and ‘public’ might just be a convention—and that new AI feature may be the least of your problems.
📅 Published on: #May 2025
📣 Hashtags: #AI #ArtificialIntelligence #Privacy #Deepfake #CyberSecurity #ChatGPT #Ris
Cybersec Investment in Europe
Section titled “Cybersec Investment in Europe”🚨 Global security trends are evolving rapidly
🔐 Cybersecurity is no longer optional, it’s foundational to business resilience and strategic growth.
| 1️⃣ | Escalating cyber threats | Risks are growing across Europe. Investments must keep pace with rising challenges. |
| 2️⃣ | Transatlantic collaboration | The USA plays a pivotal role in European security. Partnerships are essential for effective defense. |
| 3️⃣ | Strategic budgeting | Make cybersecurity a priority in your financial planning. Allocate wisely. |
| 4️⃣ | Workforce empowerment | Well-trained employees are your first line of defense. Invest in awareness programs. |
| 5️⃣ | Tailored technology | Not all solutions are created equal. Choose tools that align with your unique needs. |
| 6️⃣ | System updates | Regular patches and updates are non-negotiable to mitigate vulnerabilities. |
| 7️⃣ | Regulatory compliance | Data protection laws are stricter than ever. Stay compliant. |
| 8️⃣ | Shared responsibility | Cybersecurity isn’t just an IT issue—it’s a team effort across the organization. |
| 9️⃣ | Incident response | Breaches happen. A response plan minimizes impact and accelerates recovery. |
| 🔟 | Future agility | Stay adaptable to meet emerging threats and challenges head-on. |
📅 Published on: #April 2025
📣 Hashtags: #Cybersecurity #Cybersec #DataProtection #BusinessLeadership
